Windows Exploit Development Part III
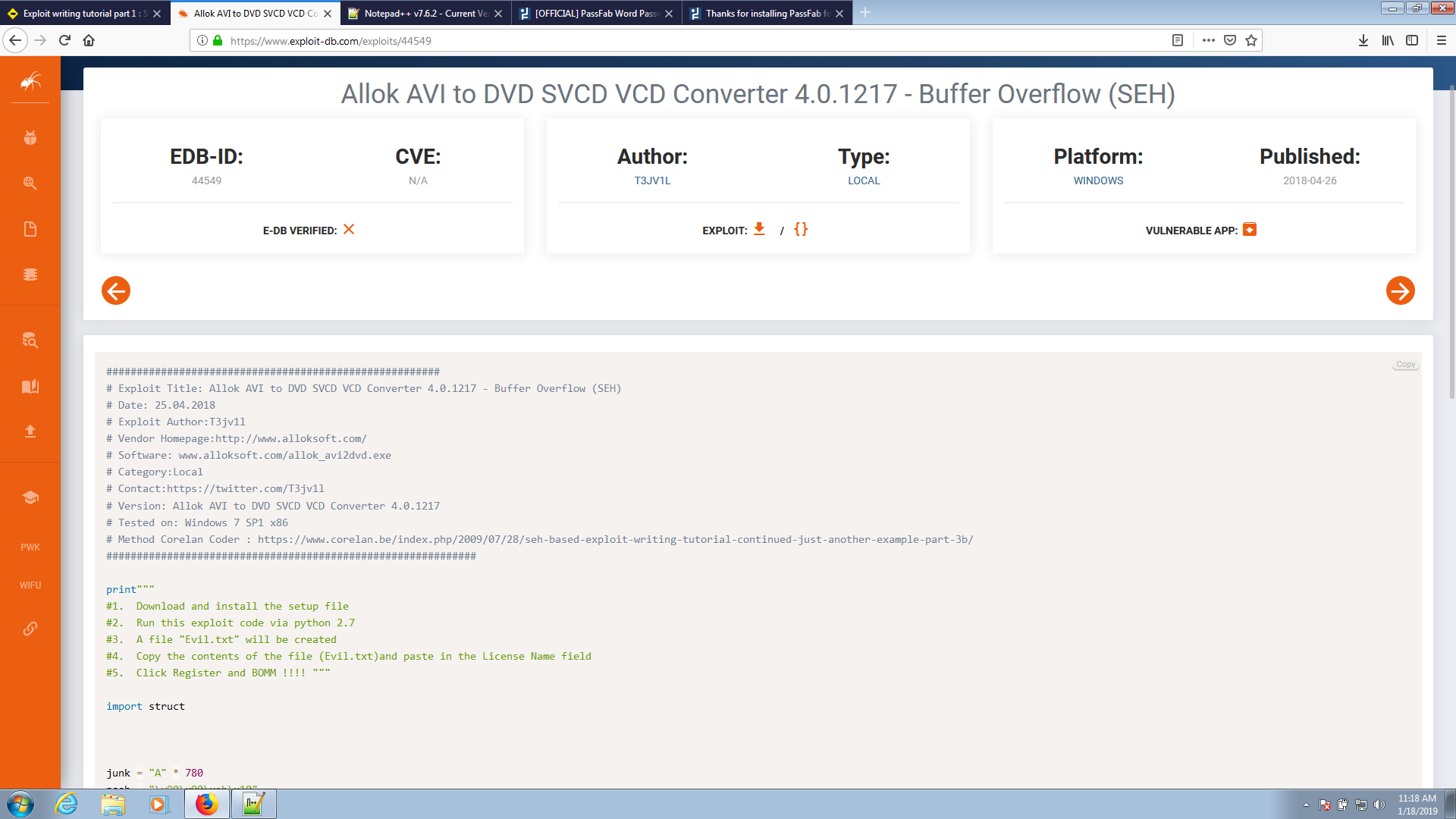
SEH Handler mechanism behind the application Hello everyone. I’ll be talking about Windows Exploit Development SEH today. The second flaw I found was in Allok Avi to DVD SVCD Converter, which you ...

SEH Handler mechanism behind the application Hello everyone. I’ll be talking about Windows Exploit Development SEH today. The second flaw I found was in Allok Avi to DVD SVCD Converter, which you ...
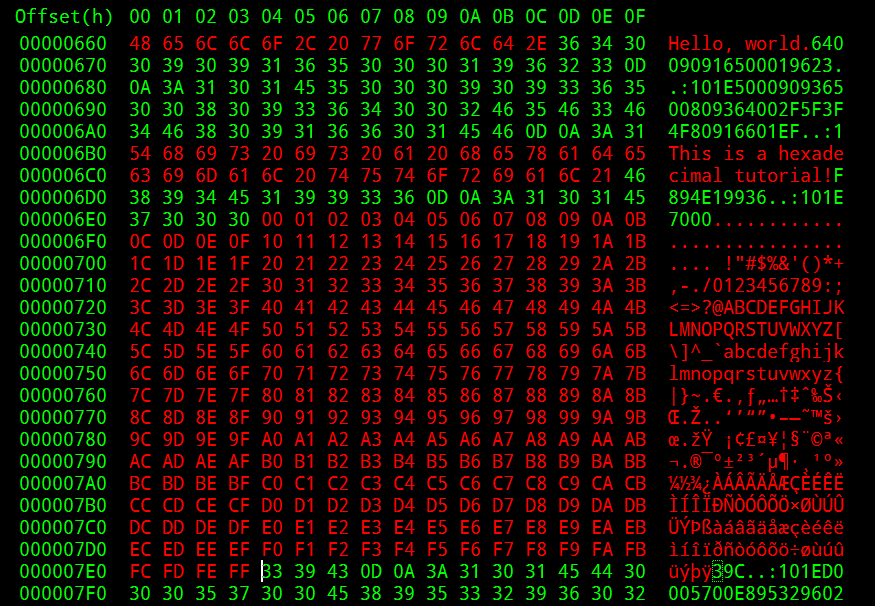
Windows Exploit Development Part II Hello everyone. Today, I’ll show you the different skills you need to create exploits. In this section, I’ll talk more about the Immunity Debugger.We will use m...
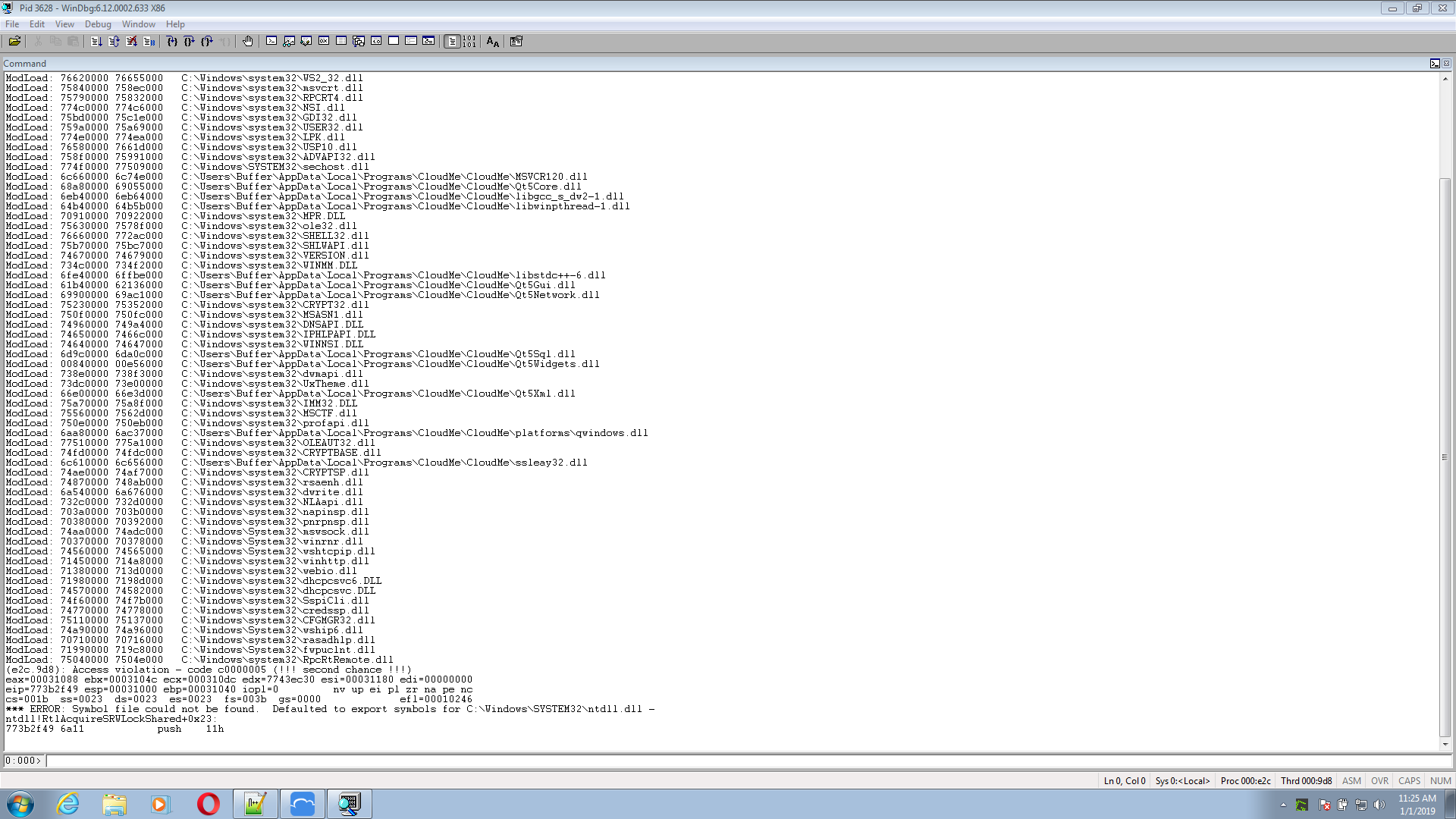
Setup Environment Hello everyone. Today, I will show you how to use WinDGB and Immunity Debugger to make a buffer overflow. I’ll pay more attention to WinDGB. WinDbg is a debugger for the Microsof...

How to Make Your Own Shellcode Part II! Hello Hackers Part two of "How to Make Your Own Shellcode. Before I start, I’d like to thank him for helping, NytroRST. Let’s get started! We will use code...

Hello everyone. Today, we’ll talk about what shellcode is and how to make it. How does Shellcode work? In hacking, a shellcode is a small piece of code that is used as the payload when a software...

Hello everyone! Today, we’re going to discuss some commands that should never be used on Linux distributions, as they can cause serious problems. Let’s take a look at a few of them: CAUTION: Never...
Hello hackers! Today, we will demonstrate how to perform an Nmap firewall scan using Iptable rules and attempt to bypass the firewall filter to perform advanced NMAP scanning. Let’s get started! F...